Conversation
|
Congratulations on your first Pull Request and welcome to the Apache CloudStack community! If you have any issues or are unsure about any anything please check our Contribution Guide (https://github.com/apache/cloudstack/blob/main/CONTRIBUTING.md)
|
|
Found UI changes, kicking a new UI QA build |
|
@acs-robot a Jenkins job has been kicked to build UI QA env. I'll keep you posted as I make progress. |
|
UI build: ✔️ |
|
Hi @Luis-3M thanks for the PR. I was stuck on how to write the tests for the same and looking at your code helps me to learn. |
|
No worries at all @neogismm - thank you. |
4bf2f2b to
1b71696
Compare
|
Found UI changes, kicking a new UI QA build |
|
@acs-robot a Jenkins job has been kicked to build UI QA env. I'll keep you posted as I make progress. |
1 similar comment
|
@acs-robot a Jenkins job has been kicked to build UI QA env. I'll keep you posted as I make progress. |
|
UI build: ✔️ |
|
@nvazquez we will keep this one open. |
|
UI build: ✖️ |
plugins/user-authenticators/saml2/src/main/java/org/apache/cloudstack/saml/SAMLUtils.java
Outdated
Show resolved
Hide resolved
|
Found UI changes, kicking a new UI QA build |
plugins/user-authenticators/saml2/src/test/java/org/apache/cloudstack/SAMLUtilsTest.java
Outdated
Show resolved
Hide resolved
plugins/user-authenticators/saml2/src/test/java/org/apache/cloudstack/SAMLUtilsTest.java
Outdated
Show resolved
Hide resolved
|
Found UI changes, kicking a new UI QA build |
|
@acs-robot a Jenkins job has been kicked to build UI QA env. I'll keep you posted as I make progress. |
|
UI build: ✔️ |
plugins/user-authenticators/saml2/src/test/java/org/apache/cloudstack/SAMLUtilsTest.java
Outdated
Show resolved
Hide resolved
plugins/user-authenticators/saml2/src/test/java/org/apache/cloudstack/SAMLUtilsTest.java
Outdated
Show resolved
Hide resolved
plugins/user-authenticators/saml2/src/test/java/org/apache/cloudstack/SAMLUtilsTest.java
Outdated
Show resolved
Hide resolved
|
@Luis-3M Code LGTM. If you can please address one code smell as suggested by Daan, that will look pefect. |
|
Thanks for your input @DaanHoogland @harikrishna-patnala . |
|
Found UI changes, kicking a new UI QA build |
|
@acs-robot a Jenkins job has been kicked to build UI QA env. I'll keep you posted as I make progress. |
|
UI build: ✔️ |
|
SonarCloud Quality Gate failed. |
|
@blueorangutan package |
|
@DaanHoogland a Jenkins job has been kicked to build packages. It will be bundled with KVM, XenServer and VMware SystemVM templates. I'll keep you posted as I make progress. |
|
Packaging result: ✔️ el7 ✔️ el8 ✔️ debian ✔️ suse15. SL-JID 3711 |
|
@blueorangutan test keepEnv |
|
@DaanHoogland a Trillian-Jenkins test job (centos7 mgmt + kvm-centos7) has been kicked to run smoke tests |
|
Trillian test result (tid-4430)
|
|
Awesome work, congrats on your first merged pull request! |
* Add EncryptedElementType key resolver to SAML plugin * saml: Fix SAML SSO plugin redirect URL (apache#6457) This PR fixes the issue apache#6427 -> SAML request must be appended to an IdP URL as a query param with an ampersand, if the URL already contains a question mark, as opposed to always assume that IdP URLs don't have any query params. Google's IdP URL for instance looks like this: https://accounts.google.com/o/saml2/idp?idpid=<ID>, therefore the expected redirect URL would be https://accounts.google.com/o/saml2/idp?idpid=<ID>&SAMLRequest=<SAMLRequest> This code change is backwards compatible with the current behaviour. * Apply backport for SAML session cookie path apache#6149 * ui: Logout before login (apache#6193) This PR calls the logout API before login, to cleanup any duplicate sessionkey, as it was done on the legacy UI: apache#4326 Fixes: apache#6127 --------- Co-authored-by: Marcus Sorensen <mls@apple.com> Co-authored-by: Luis Moreira <Luis-3M@users.noreply.github.com> Co-authored-by: Nicolas Vazquez <nicovazquez90@gmail.com>








Description
This PR fixes the issue #6427 -> SAML request must be appended to an IdP URL as a query param with an ampersand, if the URL already contains a question mark, as opposed to always assume that IdP URLs don't have any query params.
Google's IdP URL for instance looks like this:
https://accounts.google.com/o/saml2/idp?idpid=<ID>, therefore the expected redirect URL would behttps://accounts.google.com/o/saml2/idp?idpid=<ID>&SAMLRequest=<SAMLRequest>This code change is backwards compatible with the current behaviour.
Types of changes
Feature/Enhancement Scale or Bug Severity
Feature/Enhancement Scale
Bug Severity
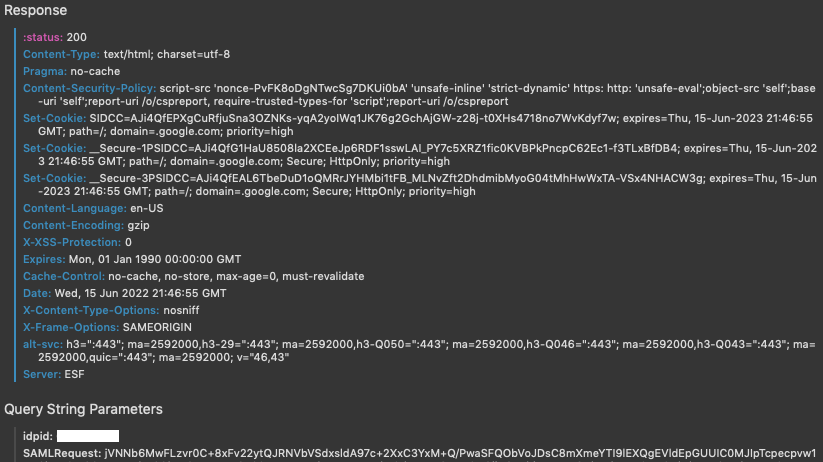
Screenshots (if appropriate):
Successful request
Unsuccessful request (due to a broken redirect URL)
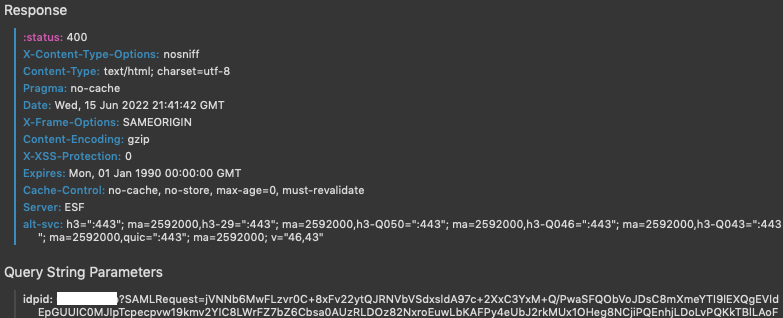
How Has This Been Tested?